Your Very Basic Cyber Security Check List Needs to Have These 5 Items
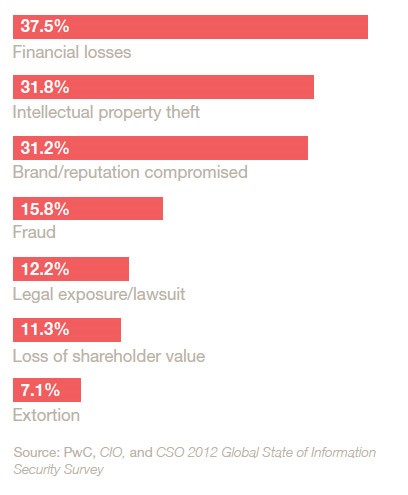
Cyber security is a trending topic, unfortunately mostly in times when a major security event has occurred. Throughout history, people are mostly alerted on a subject when a major event has taken place instead of being proactive. Targets on web vary from financial institutions to personal data but all of them have something in common, gain. By gain we don’t only mean moving money from one pocket to another. The most devastating damage and the ones an institution may never recover from, is the impact in its image. The below table by PwC shows us how the damages from cyber-attacks are distributed.
The first and most vulnerable factor in an application is the human factor. Many times you might have been prompted to choose a stronger password in a registration form. People think alike more than they know, or are willing to believe, so when the time comes to choose a password they remember, many end up choosing something that might look like “password” or “12345”. This is common knowledge among hackers (and not only) when they launch an attack. So forcing the users to choose a password with a combination of letters, numbers and symbols narrows down the possibility of success in these kinds of attacks.
In addition to human elements, software, like anything else, is never perfect. However, accumulative knowledge and years of expertise have given us tools to make a piece of software more secure than ever before. This power is something developers are aware of. Building applications using a framework, such as Symfony, Django or Spring is like using the effort and knowledge of thousands of people who had faced the same issues like yours before. In the context of cyber security these issues are not simple and are never to be taken lightly. Some issues that are very common and someone might want to look up are:
1. Cross-site scripting (XSS) is the action of injecting client-side scripts into client pages in order to run malicious code.
2. Session hijacking is the exploitation of a session to gain unauthorized access to content or services.
3. A buffer overflow is an anomaly where a program while writing data to a buffer, overruns the buffers boundary and overwrites adjacent memory locations.
4. Denial of service or distributed denial of service attack is the kind of attack that tries to make a service unavailable by overwhelming the resources that this service relies on (e.g servers).
5. SQL injection is the action of adding SQL code to web forms in order to gain access or change data.
Knowing about these threads and how they are repelled is the essence of “Knowing thy enemy”. Someone might have the incentive to offer the best service available in the web and the strength to strive for it. But ignoring those issues is jeopardizing your own efforts and putting in line your customer’s best interest along with your own professional integrity. So when acquiring a new website or software ask those questions and have the “know-how” to evaluate the correct answers.
Often, it’s a matter of just asking.
Photo by Igor Stevanovic
In addition to human elements, software, like anything else, is never perfect. However, accumulative knowledge and years of expertise have given us tools to make a piece of software more secure than ever before. This power is something developers are aware of. Building applications using a framework, such as Symfony, Django or Spring is like using the effort and knowledge of thousands of people who had faced the same issues like yours before. In the context of cyber security these issues are not simple and are never to be taken lightly. Some issues that are very common and someone might want to look up are:
1. Cross-site scripting (XSS) is the action of injecting client-side scripts into client pages in order to run malicious code.
2. Session hijacking is the exploitation of a session to gain unauthorized access to content or services.
3. A buffer overflow is an anomaly where a program while writing data to a buffer, overruns the buffers boundary and overwrites adjacent memory locations.
4. Denial of service or distributed denial of service attack is the kind of attack that tries to make a service unavailable by overwhelming the resources that this service relies on (e.g servers).
5. SQL injection is the action of adding SQL code to web forms in order to gain access or change data.
Knowing about these threads and how they are repelled is the essence of “Knowing thy enemy”. Someone might have the incentive to offer the best service available in the web and the strength to strive for it. But ignoring those issues is jeopardizing your own efforts and putting in line your customer’s best interest along with your own professional integrity. So when acquiring a new website or software ask those questions and have the “know-how” to evaluate the correct answers.
Often, it’s a matter of just asking.
Photo by Igor Stevanovic


